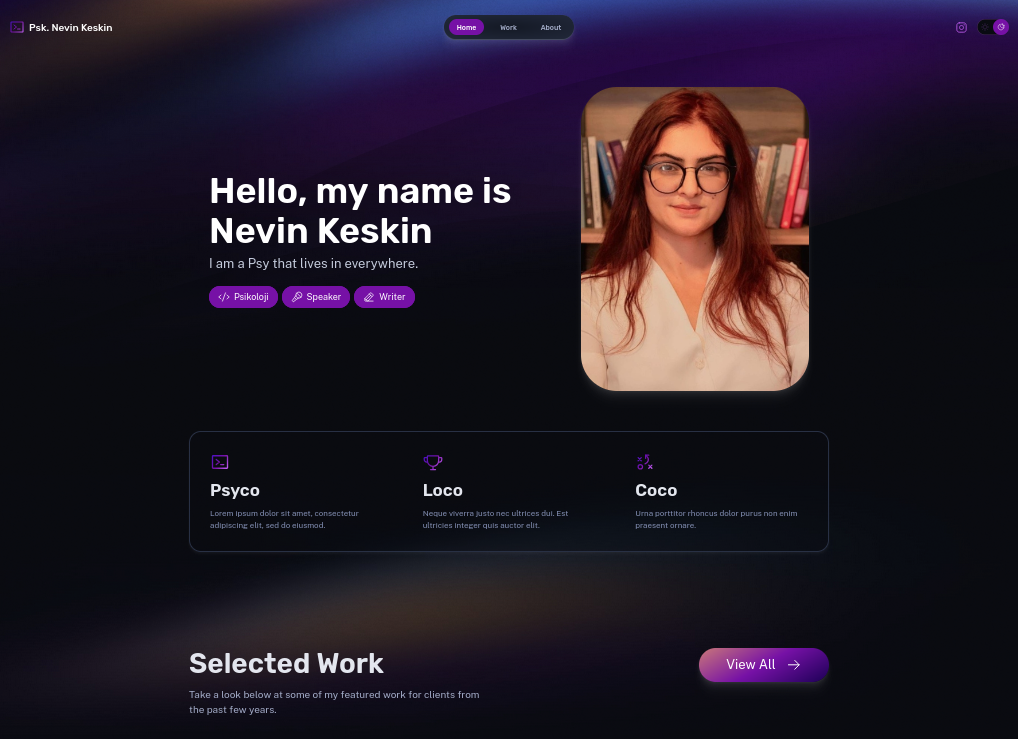
Social Auth for any SaaS x Firebase
Tl;DR
I got working a simple md editor for slidev with couple of branches to master firebase and logto SDKs for authentications.
Also, another NextJS Web App that you can use github social to login.
+++ Got Firebase and LogtoJS SDKs both working and ready to authenticate quick any webapp project.
Intro
If you are into marketing/social media and have used its related tools, you know that its a game of volume.
Say that for every 1000 cold emails you do, 2-4% will move towards the next step (and you will be lucky).
You dont want to throw away the mkt efforts, by having a landing and SaaS login that provides too much friction.
And if you have ever worked on e-commerce, you should know that a social sign in converts ~95%, instead of the ~80+% of a email/pwd.
Some people just make you signin by placing your mail and receiving a code:
With this post, lets try to understand how to make those social signins for good.
With the goal of not working our SaaS KPIs
And…in the mean time play with a wrapper of a SliDEvJS editor.
slidev buildYou can get started with such project and cursor like:
The Stack NextJS + ToastUI + SliDev.
Just as I have been using recently on the astro-editor for the multilang astro editor.
git clone https://github.com/JAlcocerT/slidev-editor
cd slidev-editor && make run-detached #localhost:3000 for the editor
# npm list -g @slidev/cli
# /usr/lib
# └── @slidev/cli@51.4.0
## docker exec -it slidev-sample sh
#docker system prune --all --volumes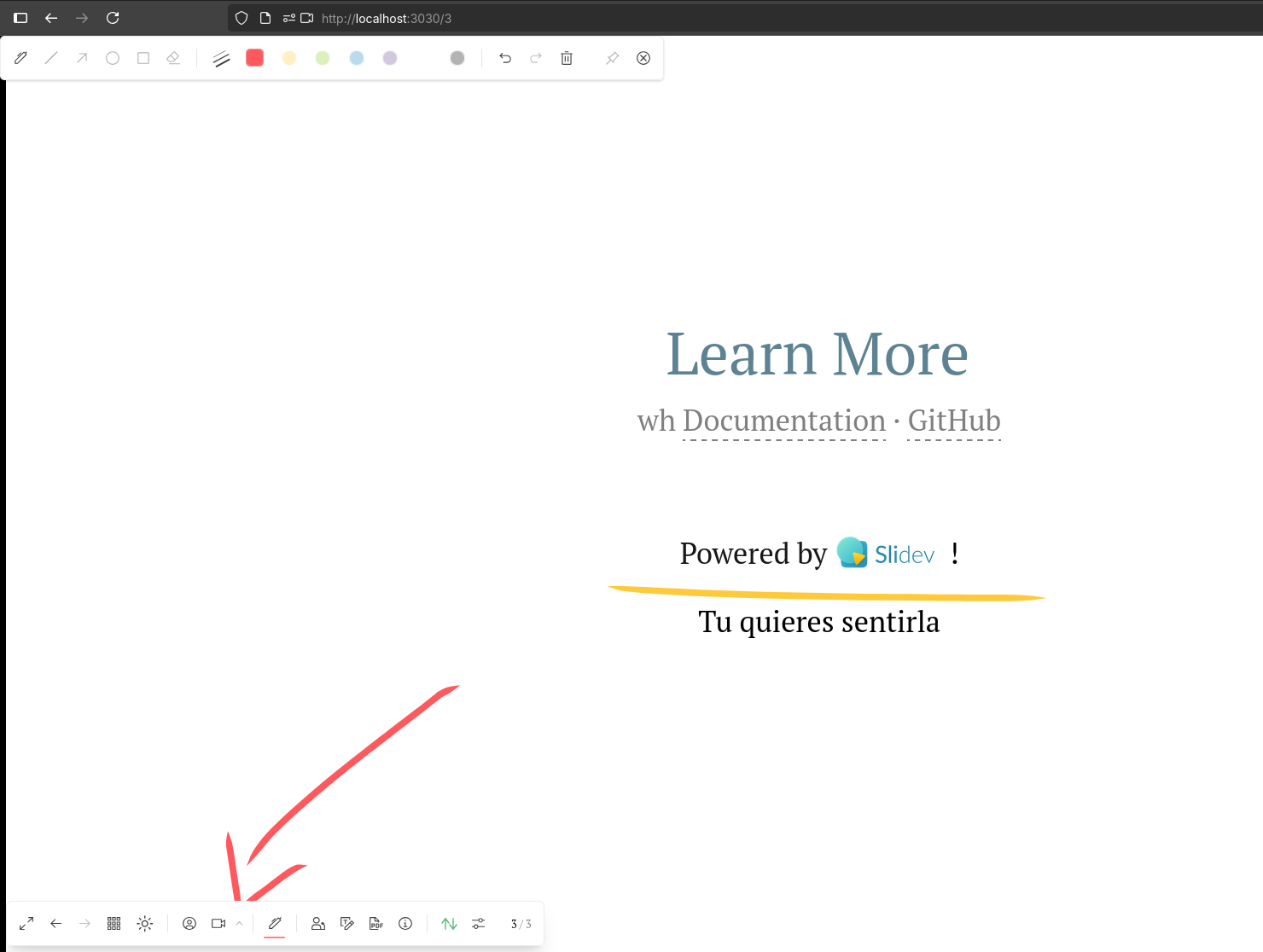
Remember you had presenter mode with SliDev at localhost:3030/presenter and you can even record your presentation
SliDev Goodies
- https://github.com/slidevjs/slidev
- https://jalcocert.github.io/JAlcocerT/creating-presentations-with-ai/#slidev
SliDev x VueJS x CSR 🚀
Yes, Slidev is a web-based presentation tool built on top of Vue.js and it primarily uses a Client-Side Rendering (CSR) approach.
It’s designed for developers to create presentations using a combination of Markdown and Vue components.
Slidev and Vue.js
Slidev is an application built with the Vue.js framework, specifically Vue 3. It leverages Vue’s component-based architecture to make the slides highly customizable and interactive. For example, you can embed your own custom Vue components directly into a slide to create live demos or interactive visualizations.
The entire presentation is a Single-Page Application (SPA) that is powered by Vue. When you create your slides in Markdown, Slidev parses the content and renders it into Vue components. This allows for features like:
- Dynamic content: You can use Vue’s data reactivity to create dynamic elements.
- Animations: It integrates with Vue’s transition system to handle slide transitions and element animations.
- Customization: You can create your own layouts and components using Vue’s syntax, giving you complete control over the design and functionality.
CSR Only?
For a typical presentation, Slidev is a CSR-only framework. When you build your presentation for production, it generates static HTML, CSS, and JavaScript files that are meant to be served from a web server.
The browser then downloads these files and renders the entire presentation dynamically on the client-side. There’s no server-side rendering (SSR) involved in the core functionality of presenting the slides.
This CSR approach is what makes Slidev presentations so portable.
They can be hosted on any static hosting service like GitHub Pages or Netlify, and they don’t require a dedicated backend server to run.
The entire logic for navigating slides, playing animations, and handling interactive elements resides in the client’s browser.
CTRL Shift P -» Mermaid Preview Diagram
Katex: so that you get good looking expressions $CAGR = \left( \frac{V_f}{V_i} \right)^{\frac{1}{t}} - 1$.
Monaco Editor: yea…the one I used here as simple .md editor
More on Monaco Editor and CSR 📌
Client-Side Rendering (CSR): The entire editor is built on client-side rendering.
The browser downloads the necessary JavaScript and CSS files, and the editor is then constructed and rendered dynamically on the web page.
There is no server-side rendering involved in the editor’s core functionality itself.
The Monaco editor itself does not have a built-in runtime environment to execute the code.
Its sole purpose is to provide a rich code-editing experience in the browser.
- The Editor Itself is Client-Side
The entire Monaco editor interface—the text, syntax highlighting, autocompletion, and even the diagnostics (the red squiggly lines for errors)—is a result of Client-Side Rendering (CSR). The JavaScript and TypeScript code that makes the editor work runs directly in your browser. This includes the “language services” that provide the intelligent features, which are often run in a Web Worker to avoid freezing the main browser thread.
However, this is all static analysis of the code, not execution. The editor understands the syntax and structure of the code, but it doesn’t run it.
- Runtime Environment is a Separate Component
To actually execute the code written in the Monaco editor, you need to connect it to a separate runtime environment. This can be done in two ways:
In-Browser Execution (for JavaScript/TypeScript): You can use the browser’s native JavaScript engine to run the code. This is how many online code sandboxes or playgrounds work. When you click “Run,” the website takes the code from the editor and either puts it into an
<iframe>or runs it directly in the main browser context, displaying the output in a separate console-like area. This is a form of CSR, but it’s separate from the editor’s core function.Server-Side Execution (for other languages): For languages like Python, C++, Java, or even Node.js, the code must be sent to a backend server. This server would have the necessary runtime and security sandboxing in place to execute the code and return the output. This is the most common approach for online coding challenges or platforms like Replit and Glitch. The server handles all the actual execution, while the browser only handles the input (the editor) and output.
BaaS
Many popular Backend-as-a-Service (BaaS) platforms offer Google social sign-in.
This is a common and important feature for user authentication.
The most prominent players in this space are Firebase Authentication, Supabase, and PocketBase.
Once the main branch was ready with some SliDev Editor PoC working powered by NextJS…
It was time to do some git branching…
git branch -a
#create a new branch from main
git checkout -b firebaseauth main #git checkout -b <new-branch-name> main
#git checkout main && git pull origin main
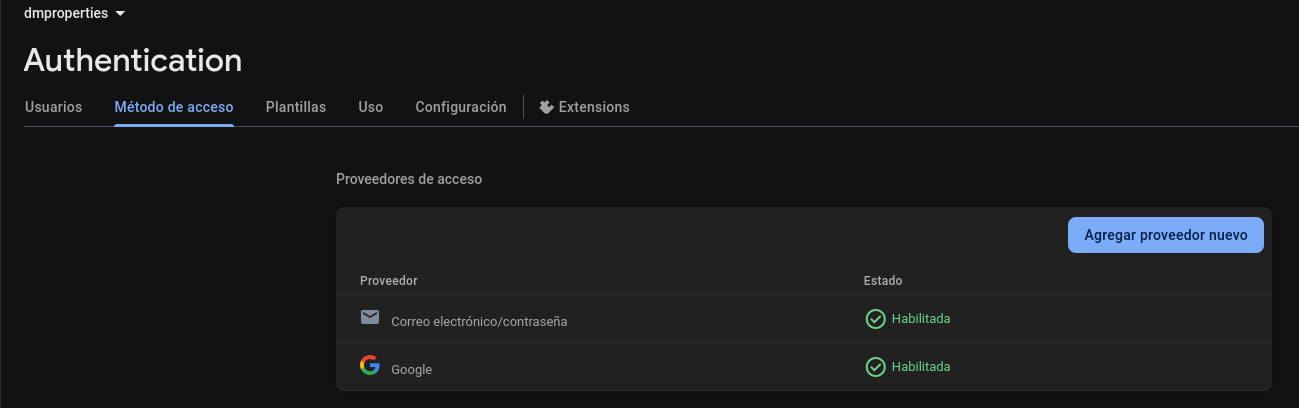
#git checkout -b business-feature1. Firebase Authentication 🤖
Firebase Authentication is a Backend-as-a-Service provided by Google, so it naturally has deep integration with Google Sign-in.
It provides a robust, pre-built authentication system that is easy to integrate into web and mobile apps. It supports various sign-in methods, including Google, Facebook, Twitter, and email/password.
Its tight integration with other Firebase services like Firestore and Cloud Functions makes it a popular choice for developers already in the Google ecosystem.
Pros:
- Extremely easy setup for Google Sign-in.
- Generous free tier for getting started.
- Seamless integration with the entire Firebase suite.
- Managed and scalable, so you don’t have to worry about infrastructure.
Cons:
- Vendor lock-in to the Google ecosystem.
- Can become expensive at scale depending on your read/write operations.
- Uses a NoSQL database (Firestore), which can be a limitation for projects requiring complex relational queries.
Firebase Auth branch with Cursor 🚀
I have just created a new branch to experiment with firebase authentication
can you create a z-firease-auth.md to explain what I need to get from google to get this going?
and also implement a email/password sign in sign up, which also will allow for google social signin?
the landing page should be visible for all, and the demo presentation as well, but the editor itself it has to be auth protected
for now, all users will see the very same editor
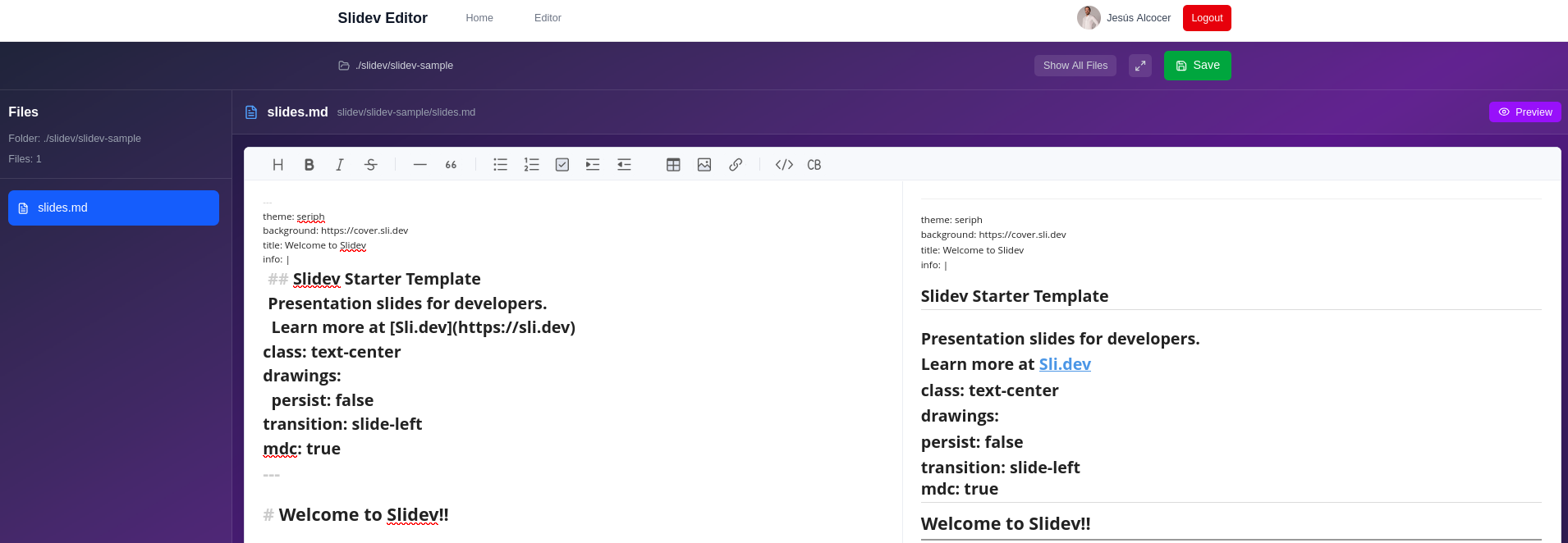
#git clone https://github.com/JAlcocerT/slidev-editor ./slidev-editor-firebasebranch
#cd slidev-editor-firebasebranch
git branch -a
git checkout firebaseauth #this brings the remote branch to your PCGet your Firebase Setup and fill the env.local: https://github.com/JAlcocerT/slidev-editor/blob/firebaseauth/.env.example
#nano .env.local
#npm run dev
#docker compose build slidev-editor
make run #or make run-detached
As this was the 3rd time I did this, it was 2 min, instead of the initial 45 and the 5 min later on.
BTW: email verification when not doing the social signup also working (goes to spam though) from domain dmproperties.firebaseapp.com
https://jalcocert.github.io/JAlcocerT/stonks/#astro-x-data-x-chartjs https://jalcocert.github.io/JAlcocerT/firebase-auth-101/
And for the server x300:
#docker compose -f docker-compose.server.yml up --build
docker compose -f docker-compose.server.yml up --build -d
#docker network connect cloudflared_tunnel slidev-editor #network -> container name
docker inspect slidev-editor --format '{{json .NetworkSettings.Networks}}' | jq #publish it via Zero Trust with pystonks-app-streamlit:8501With that ready, just do your CF setup: slidev-editor:3000
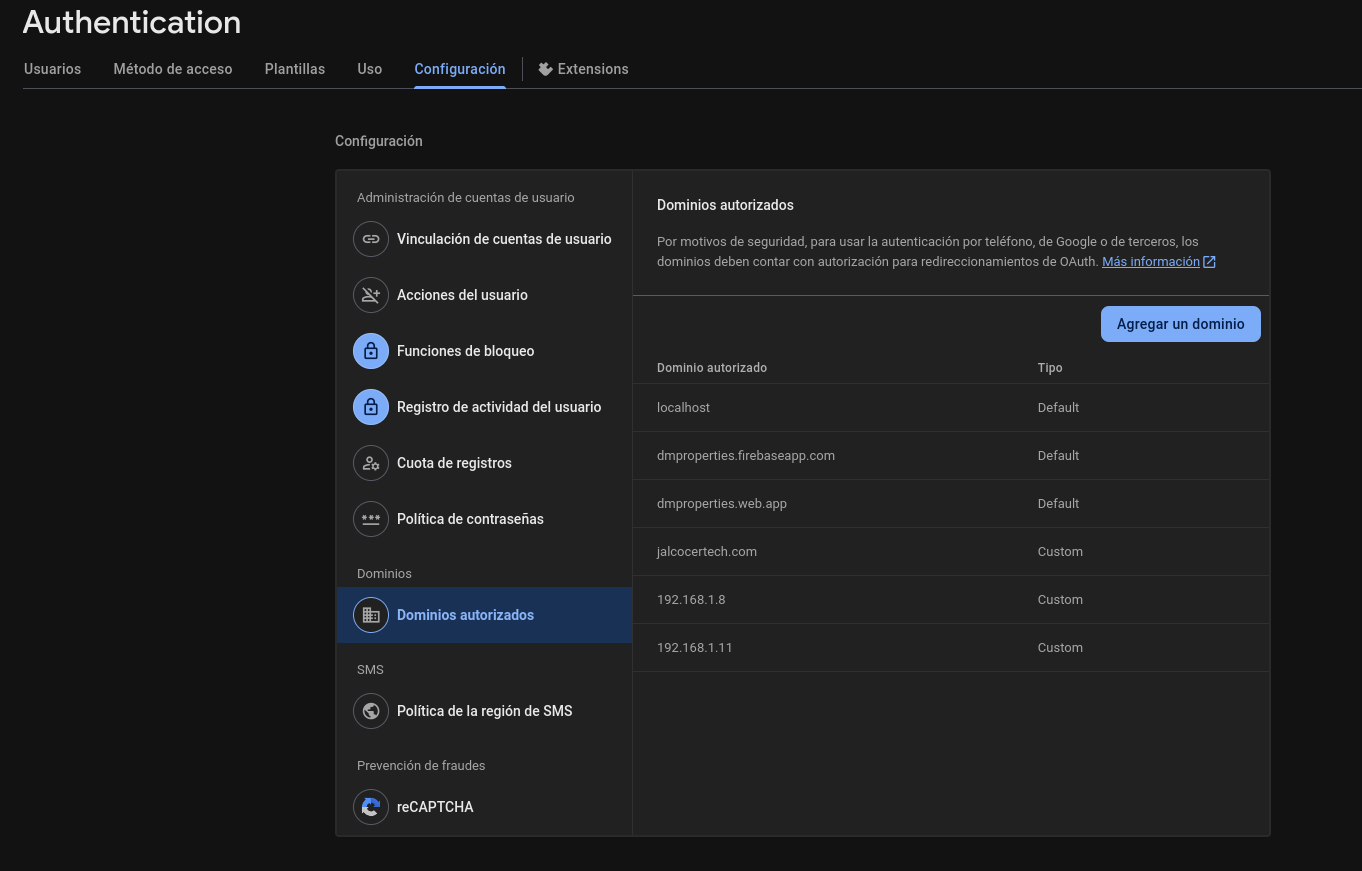
Firebase x Particular User Admin Page
You can direct a user to a specific, personalized URL (/admin/useremail) in a Next.js app after they sign in with Firebase Auth.
You’ll use Firebase Auth on the client side to get the user’s information and then use Next.js’s routing to redirect them.
To ensure that only they can see that page, you’ll need to implement client-side and server-side route protection.
Yes, what you’ve described is a standard and secure way to build this kind of application using Firebase Auth and Next.js.
The approach is secure because it relies on both client-side and server-side checks.
- Client-Side Protection
The client-side logic in your Next.js app ensures that a user is redirected away if their email doesn’t match the one in the URL or if they’re not signed in.
While this provides a good user experience, it’s not foolproof on its own. A malicious user could bypass it by disabling JavaScript in their browser. This is why the server-side check is so crucial.
- Server-Side Protection
The real security comes from the server-side check using Next.js’s getServerSideProps and the Firebase Admin SDK.
- Verification: When the page is requested, the
getServerSidePropsfunction on the server verifies the user’s ID token. The ID token is a JWT (JSON Web Token) that proves the user’s identity. It’s signed by Firebase and is tamper-proof. - Trust: Your server trusts Firebase to verify the token’s authenticity. It’s not just checking an email from the URL, but it’s verifying a cryptographically signed token that proves the user’s identity and confirms that they are the person they claim to be.
- Conditional Rendering: If the token is invalid, expired, or doesn’t match the user in the URL, the server simply refuses to render the page and redirects the request to a login page. This prevents unauthorized content from ever reaching the user’s browser, making it highly secure.
In short, the combination of Firebase Authentication on the client side for user sign-in and the Firebase Admin SDK on the Next.js server for token verification creates a robust and secure system.
Firebase x Particular users SignUp
This must be done within your code, not in the Firebase Web UI.
While the Firebase console allows you to enable or disable different sign-in methods (like Email/Password, Google, etc.), it does not have a feature to restrict user sign-ups to a specific list of emails.
This is a deliberate design choice because relying on client-side logic for such a critical security task is not secure. A malicious user could easily modify the client-side code to bypass the check.
You need to implement the whitelist logic on a trusted server-side environment, which is where Firebase Cloud Functions come in.
Why the Code-Based Approach is Secure
The process for securely implementing an email whitelist in Firebase is as follows:
Firebase Database (e.g., Firestore): You’ll first store your list of whitelisted emails in a secure collection in Firestore. You would then write security rules to ensure that only an authenticated admin can read or write to this list.
Next.js App (Client-side): When a user attempts to sign up with their email and password, your Next.js app does not call the
createUserfunction from the client-side Firebase SDK. Instead, it makes a request to a Cloud Function.Cloud Function (Server-side): This is the core of the secure setup.
- The function receives the email and password from your Next.js app.
- It uses the Firebase Admin SDK to query your Firestore database to check if the submitted email exists in your whitelist.
- Only if the email is found on the whitelist does the Cloud Function proceed to use the Admin SDK’s
createUsermethod to create the new user account in Firebase Authentication. - If the email is not on the whitelist, the function returns an error, and no account is created.
This method is secure because the user creation logic is entirely handled on a trusted server (the Cloud Function) where a user has no way of interfering with the process.
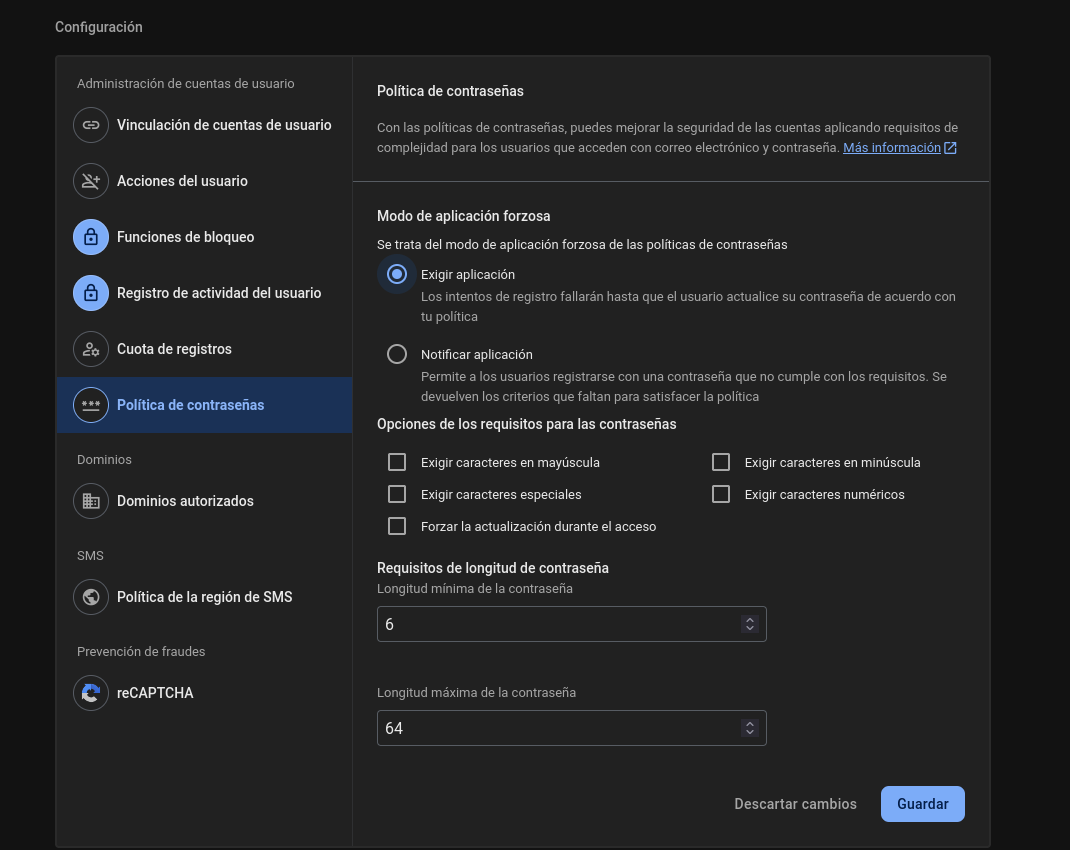
Firebase can be configured to allow sign-up and sign-in only for particular emails, but it isn’t a built-in feature you can simply toggle in the Firebase console.
You have to implement this logic yourself using a combination of Firebase services, which makes the process secure.
The Problem
By default, when you enable the Email/Password sign-in method in Firebase Auth, any user can create an account with any email address.
You can’t just provide a list of approved emails and have Firebase automatically block others.
The Secure Solution 🔒
To securely restrict sign-ups to a specific list of emails, you’ll need to use two key Firebase features: Cloud Functions and a Database (Firestore or Realtime Database).
Step 1: Create a Whitelist in Your Database
First, create a collection or a node in your Firebase database to store a list of pre-approved emails. Only an admin user should have read/write access to this list through your admin panel.
Example Firestore Structure:
/approvedEmails
- "user1@example.com": true
- "user2@example.com": trueStep 2: Use a Cloud Function for User Creation
Instead of allowing users to sign up directly from your Next.js app, you’ll create a Cloud Function.
This function will act as a secure intermediary for all sign-up requests.
- When a user submits their email and password from your app, the app will call this Cloud Function.
- The Cloud Function will receive the email and password.
- It will then check the user’s email against the approved email whitelist in your database.
- If the email is on the list, the Cloud Function will use the Firebase Admin SDK to create the user account directly on the server.
- If the email is not on the list, the function will return an error, preventing the user from being created.
This approach is highly secure because it moves the user creation logic to a trusted server environment (the Cloud Function).
The client app never has the permission to create users directly, so even if a malicious user tampers with the front-end code, they cannot bypass your whitelist.
Step 3: Implement Client-Side Sign-in
Once the user account has been successfully created via the Cloud Function, your Next.js app can proceed with the normal Firebase sign-in process.
Since the account now exists, Firebase Auth will handle the rest.
Even if a user with an unapproved email manages to sign up, they won’t be able to access any of your application’s data if you have also correctly configured Firebase Security Rules that check for a specific email or a custom claim that you set on approved users.
2. Supabase 🚀
Supabase is an open-source alternative to Firebase, often referred to as “Firebase for PostgreSQL.”
It provides a full suite of BaaS features, including authentication, a real-time database, and serverless functions.
Supabase Auth supports various social providers, including Google.
Because it’s open-source and uses a relational database (PostgreSQL), it gives developers more flexibility and control.
Pros:
- Open-source, which offers flexibility and the ability to self-host.
- Uses PostgreSQL, a powerful and widely-used relational database.
- Has a built-in authentication system that integrates seamlessly with its database using Row Level Security (RLS).
- Predictable pricing and a clear path to self-hosting.
Cons:
- A newer platform compared to Firebase, so its feature set is still maturing.
- Can have a steeper learning curve for developers not familiar with PostgreSQL.
3. PocketBase ⚡
PocketBase is a unique, lightweight BaaS platform packaged as a single-file binary that includes a Go backend and an embedded SQLite database.
It’s a great choice for quick prototypes and small-to-medium-sized applications.
PocketBase supports OAuth2 authentication, which means you can easily implement Google Sign-in.
Because it’s self-hosted, you have full control over your data and infrastructure.
Pros:
- Extremely simple and fast to deploy (just one file).
- Built-in features (auth, database, file storage) work out of the box.
- Free to use (you only pay for your hosting costs).
- Offers a real-time API out of the box.
Cons:
- Not a managed service, so you are responsible for hosting, scaling, and backups.
- The embedded SQLite database may not be suitable for large-scale, high-concurrency applications.
- Doesn’t have a built-in serverless functions feature like Firebase or Supabase.
You can even combine Pocketbase users collection to help you signup/in users into your streamlit web apps:
See this script that leverages https://pypi.org/project/streamlit-authenticator/ with the Pocketbase collection.
AaaS
When you need robust user management, including social sign-in and email verification, but don’t need the entire suite of backend services (like a database, file storage, etc.), you’re looking for an Authentication-as-a-Service (AaaS) or Identity and Access Management (IAM) provider.
These services specialize in handling user authentication and authorization, and they often integrate with your existing backend and application architecture.
1. Clerk 💼
Clerk is a modern and developer-friendly platform that focuses on providing a seamless, full-stack user management experience.
It’s particularly popular with front-end developers using frameworks like Next.js, as it provides pre-built, customizable UI components for sign-up, sign-in, user profiles, and more. It offers a generous free tier and is known for its excellent developer experience.
- Key Features:
- Pre-built UI components: This is a huge time-saver. You can drop in components for authentication flows, user profiles, and organization management.
- Full-stack integration: It provides SDKs for both front-end and back-end frameworks, ensuring secure and seamless authentication.
- Extensive authentication methods: Supports Google, GitHub, and other social sign-ins, along with email/password, magic links, and more.
- Email and SMS verification: Built-in email verification and password reset flows.
2. Okta 🏢
Okta is a massive, enterprise-grade identity platform.
It’s a leader in the IAM space, focusing on both workforce identity (managing employee access) and customer identity (CIAM) for your applications.
Okta’s solutions are incredibly comprehensive, scalable, and secure. They offer a huge range of features, from simple social login to complex B2B authentication and single sign-on (SSO).
- Key Features:
- Enterprise-grade security: Provides robust features like multi-factor authentication (MFA), threat detection, and advanced session management.
- Highly customizable: You can configure authentication flows with “rules” and “hooks” to fit complex business logic.
- Wide protocol support: Supports all major identity protocols, including OAuth 2.0, OpenID Connect (OIDC), and SAML.
- Extensive integrations: Integrates with thousands of applications and services out of the box.
- Email verification: Handles email verification and other user management tasks.
3. Auth0 (by Okta) 🚀
Auth0 was acquired by Okta and is often considered the developer-centric, more flexible arm of the company.
It’s known for its powerful, yet easy-to-use platform that allows developers to add authentication and authorization to their applications with minimal effort. It’s a great middle ground between the full BaaS platforms and the more complex enterprise solutions.
- Key Features:
- Universal Login: Provides a customizable hosted login page, so you don’t have to build your own UI.
- Actions and Rules: Allows for deep customization of the authentication flow using serverless functions.
- Wide range of social connections: Supports Google and many other social providers, including enterprise connections.
- Email verification: Built-in and configurable email verification and password reset flows.
4. Logto 🦊
Logto is a strong, open-source alternative to the proprietary AaaS platforms.
It’s a self-hostable identity platform that provides a complete set of features for authentication and user management.
Because it’s open-source, it’s a great choice for developers who want more control over their data and infrastructure without the vendor lock-in of a managed service.
Modern auth infrastructure for developers
Logto adds multi-tenancy, enterprise SSO, and RBAC to your SaaS or AI apps. All with OIDC and OAuth 2.1 made simple, fast, and developer-friendly.
- Key Features:
- Open-source and self-hostable: Gives you full ownership and control.
- All-in-one: Includes authentication, authorization, user management, and multi-tenancy.
- Framework-free: Provides SDKs for a wide range of languages and frameworks.
- Customizable login experiences: You can tailor the user-facing parts of the platform to match your brand.
Few months back, I tested Logto Python SDK: here and here
It was working perfectly, as you can see on the related source code:
 WebGenerAItor
WebGenerAItorBut I want to compare kneck to kneck with couple of new auth architectures ive been learning along the way.
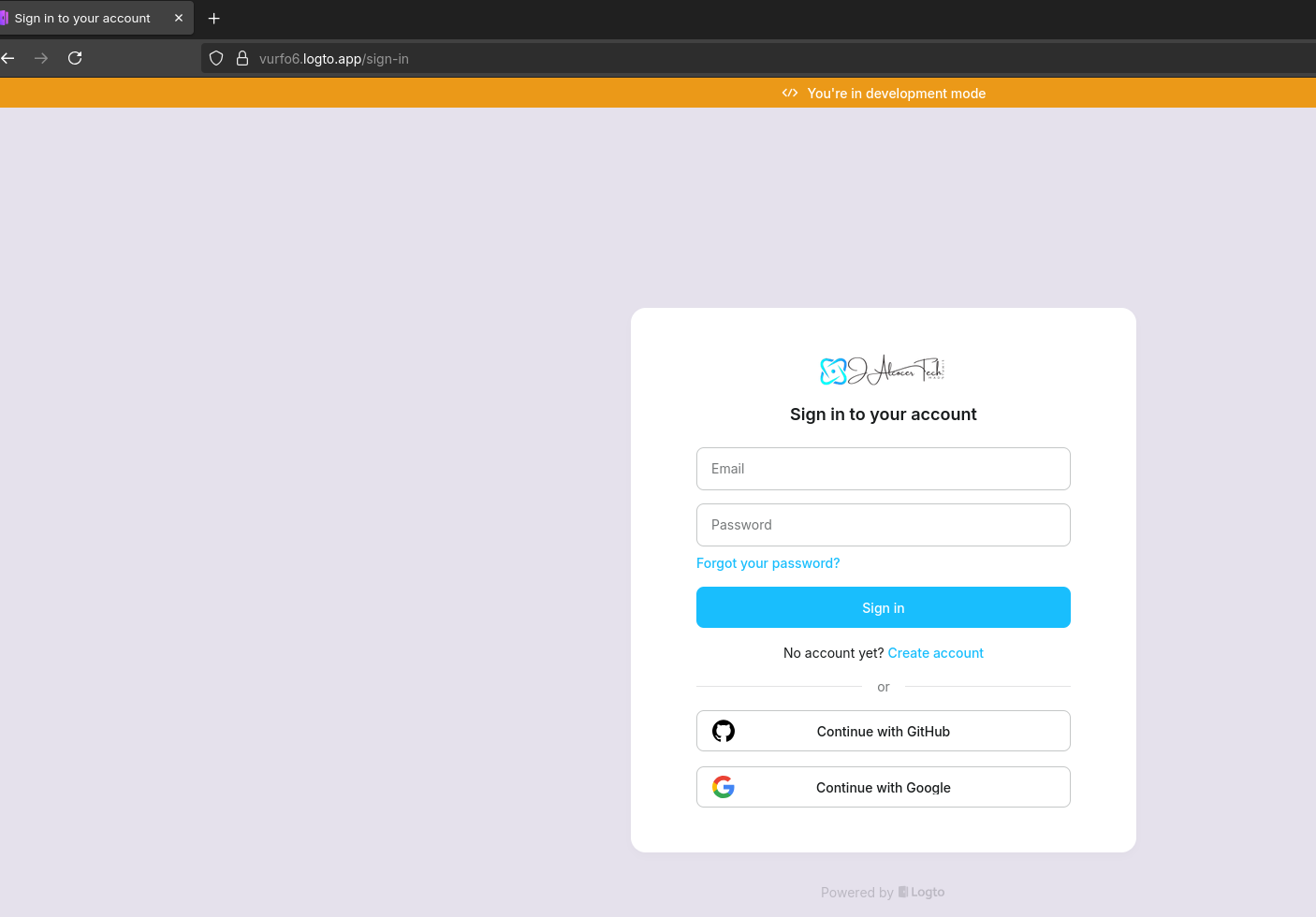
So switch to the LogtoJS branch and let’s get to it:
git branch -a
#create a new branch from main
git checkout -b logtojseauth main #git checkout -b <new-branch-name> main
#git checkout main && git pull origin mainI was prompting the agents with sth like:
and can we implement similar setup to the firebase authentication, but with LogtoJS?
Add a `z-logto-setup.md` explaining what I need to do from logto web UI and also create the required `env.sample`npm install @logto/next
I selected Traditional Web and got the credentials for LogTo:
# Logto Endpoint - Your Logto instance URL
NEXT_PUBLIC_LOGTO_ENDPOINT=https://your-domain.logto.app
# Logto App ID - Found in your application settings
NEXT_PUBLIC_LOGTO_APP_ID=your-app-id-here
# Logto App Secret - Found in your application settings (keep this secret!)
LOGTO_APP_SECRET=your-app-secret-hereRemember about setting up right redirect URIs:
http://localhost:3000/callback
http://localhost:3000/api/logto/sign-in-callback
#for prod
https://yourdomain.com/callback
https://yourdomain.com/api/logto/sign-in-callback
Then, you will get your vibe coded logto setup to work:
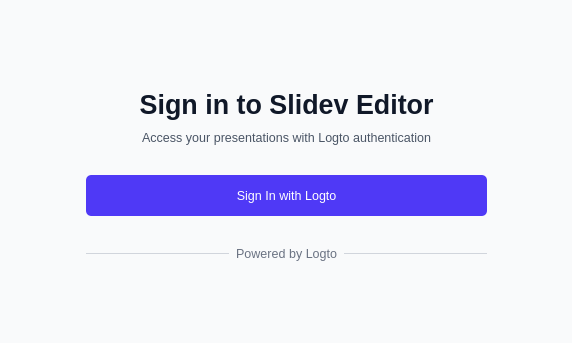
Logto will validate your signin with an email from: no-reply@logto.email
And you can also vibe code your way to a localhost:3000/debug in case sth goes wrong:
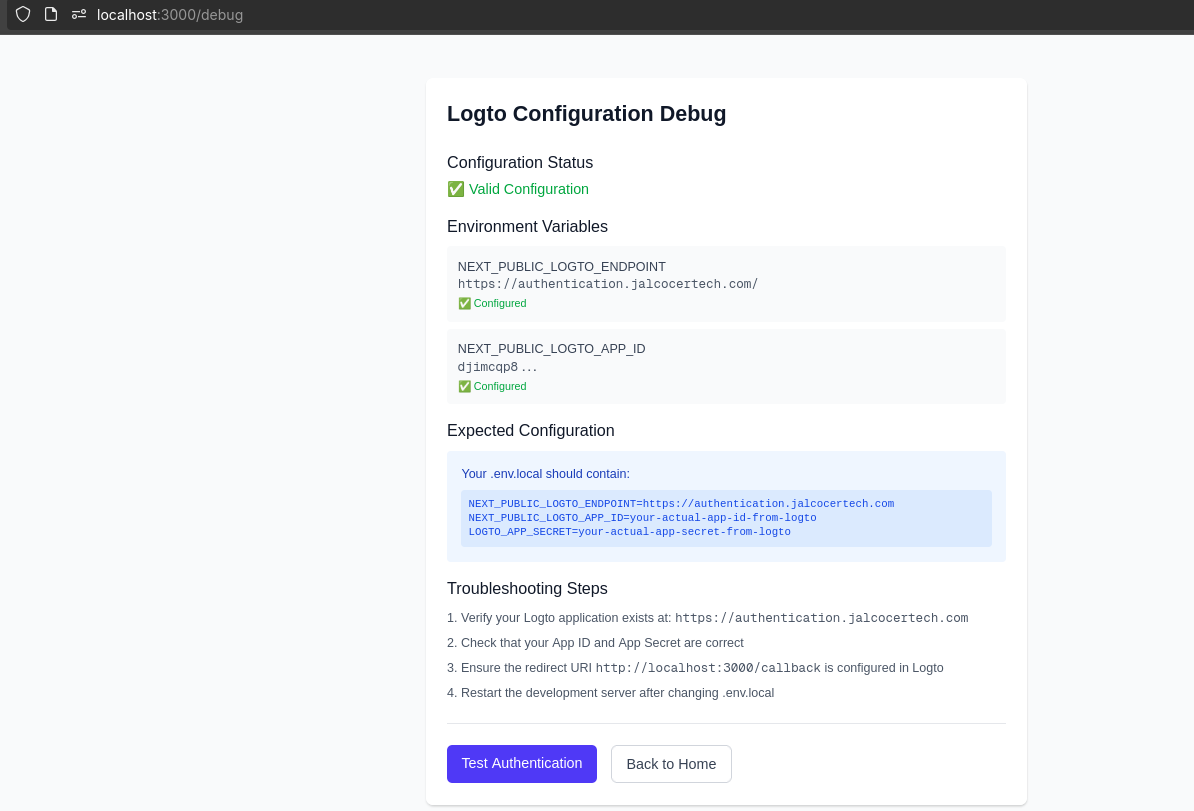
Make sure to understand the difference of Traditional Web (MPA) vs SPA, as I had to do at this .md
The final Logto + NextJS setup worked for me via the SPA way!
The .env.local required for this is just:
NEXT_PUBLIC_LOGTO_ENDPOINT=https://authentication.jalcocertech.com
NEXT_PUBLIC_LOGTO_APP_ID=your-actual-app-id-from-logto
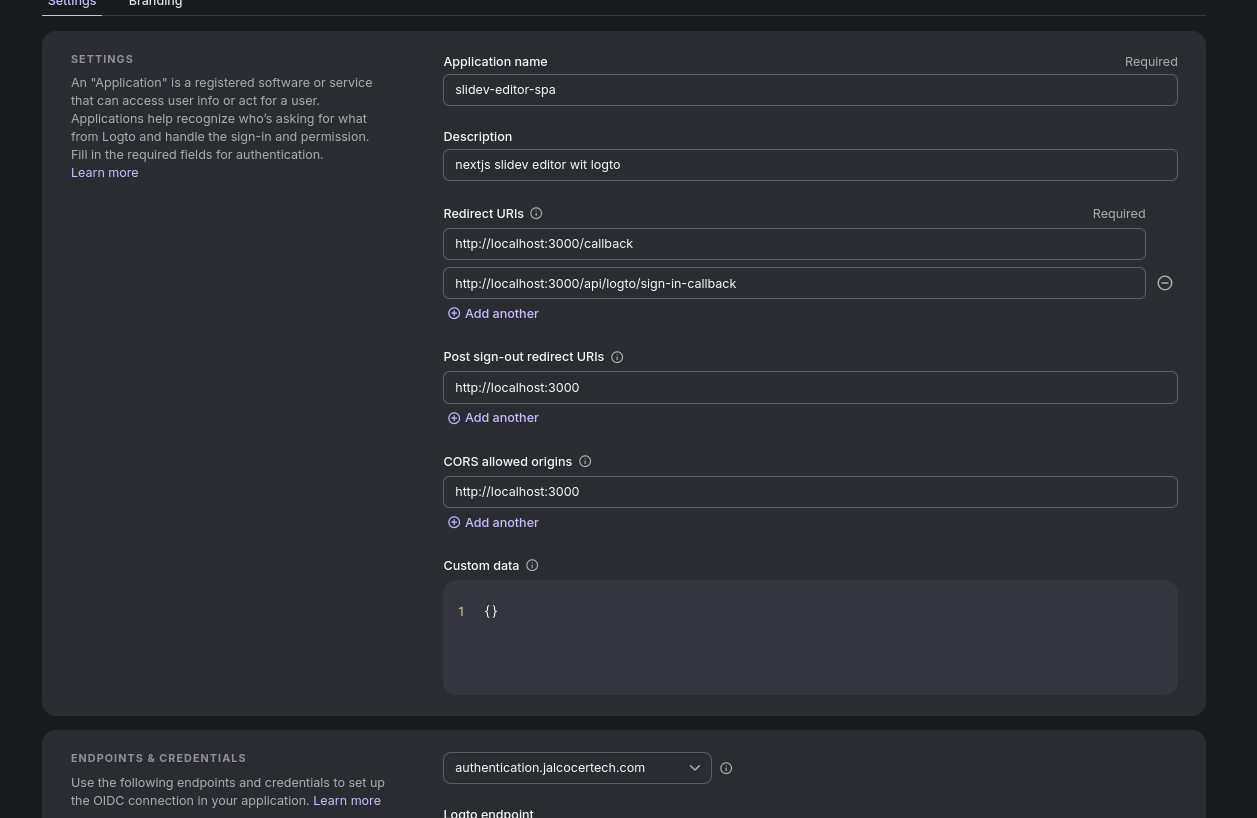
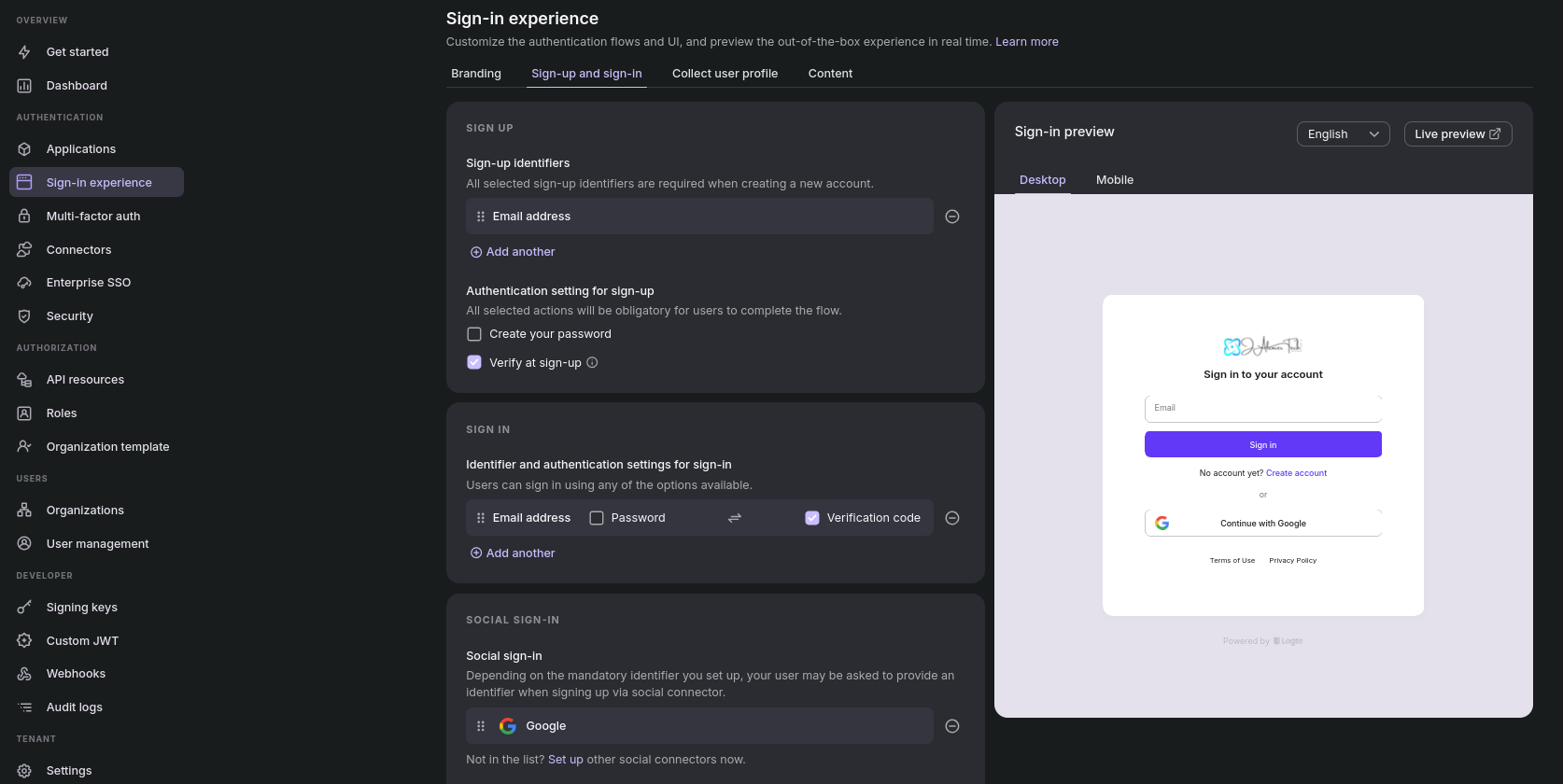
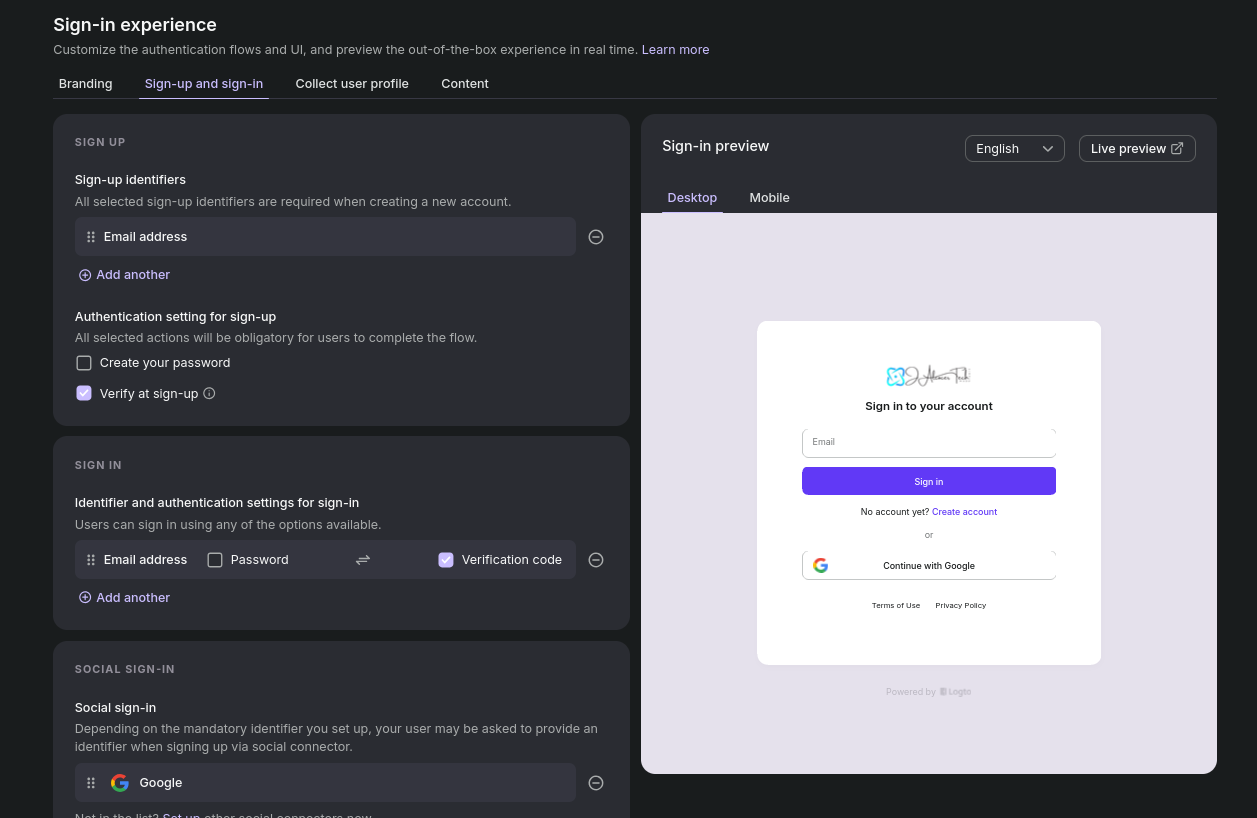
I would recommend to keep the Logto with the email + Code to confirm. See Sign in experience and Connectors section.
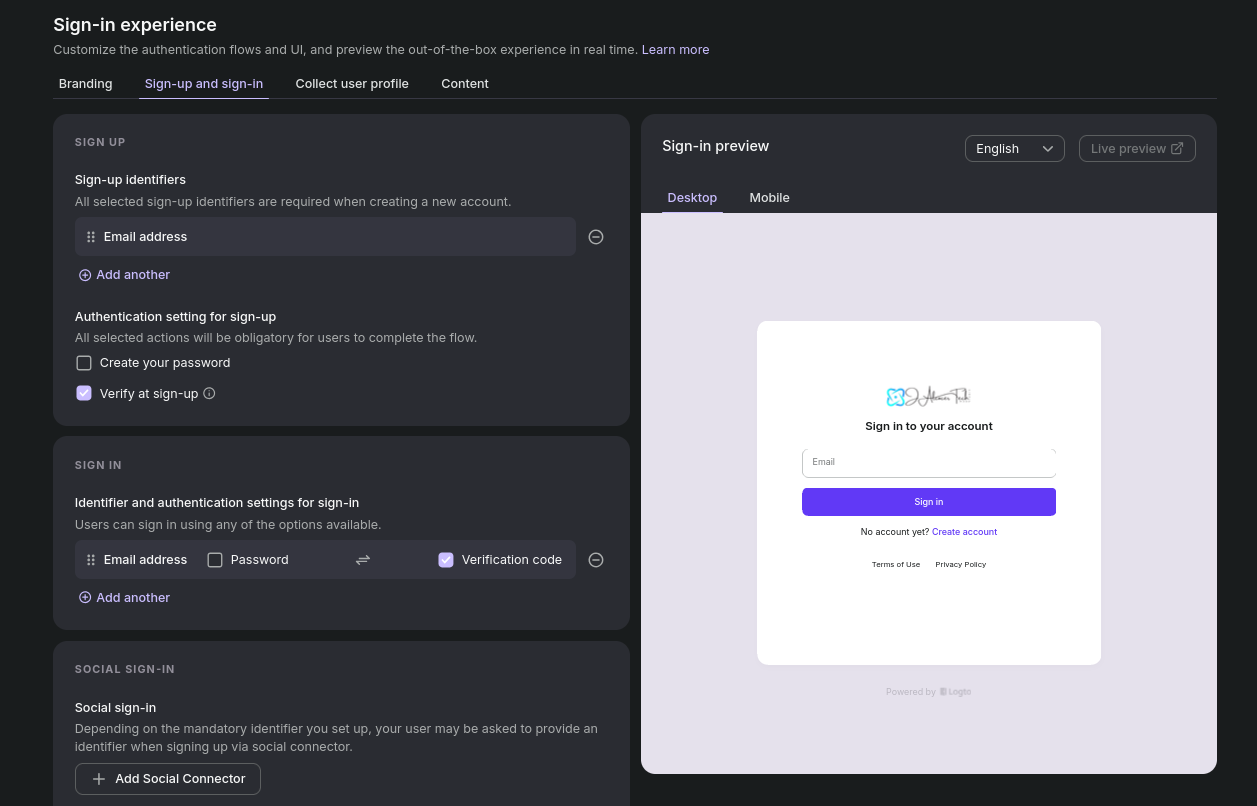
YOu could also do email/user + pwd or social signin (for example with google)
You can create a script to pull registered users from Logto
Within logto UI, they are at
User management
Conclusions
Because https://gamma.app/ does not have to be the only one doing nice stuff.
Gamma is your AI design partner for effortless presentations, websites, social media posts, and more—so you can focus on what you do best.
Social Signin > One Time Link > Email and PWD
Firebase Auth with email/pwd + social signin working on desktop and mobile ✅
Also Logto with the email + received code to login ✅
Both to the email validation for you!
Earlier this year I read a post which motivated me to create this - https://darko.io/posts/but-auth-is-hard
- Github Social sign in ✅
Logto vs FirebaseAuth vs PB SDK for Auth… 📌
Logto, Firebase Authentication, and PocketBase SDK implement authentication differently, with distinct approaches, features, and use cases.
Logto Authentication
- Logto is an open-source identity infrastructure focused on secure, standards-based authentication using OAuth 2.1 and OpenID Connect (OIDC).
- It supports web, mobile, desktop, machine-to-machine (M2M) authentication, and third-party application integration as an Identity Provider (IdP).
- Logto provides protocol-compliant flows with social login, user management, multi-tenancy, RBAC, and supports SAML apps for enterprise SSO.
- Integration involves using SDKs or no-code solutions, handling sign-in, sign-out, and user info with API routes and tokens.
- It also offers a Management API for advanced customization and automation.
Pros:
- Open-source, protocol-compliant with OAuth 2.1 and OIDC.
- Supports complex enterprise use cases like SAML SSO, RBAC, multi-tenancy.
- Flexible for machine and user authentication.
- Good for SaaS and AI apps needing secure, scalable auth.
Cons:
- Requires understanding of OIDC/OAuth protocols.
- More setup complexity than turnkey solutions.
- Newer ecosystem, less documentation and community compared to Firebase.
Firebase Authentication
- Firebase Auth is a widely-used backend service with SDKs and ready-made UI libraries for authenticating users via email/password, phone, and social providers like Google and Facebook.
- Offers FirebaseUI for drop-in auth flows and supports custom backend integration using industry standards OAuth 2.0 and OIDC.
- The Identity Platform upgrade adds enterprise features like multi-factor authentication, blocking functions, audit logging, multi-tenancy and SAML/OpenID Connect providers.
- Handles token issuance, session management, and user state tracking transparently.
Pros:
- Mature, battle-tested with extensive documentation and community.
- Easy to set up with ready-to-use UI and SDKs.
- Deep Firebase ecosystem integration (database, storage, etc.).
- Enterprise-grade features available with upgrade.
Cons:
- Vendor lock-in to Google Firebase.
- Pricing can rise steeply with scale and advanced features.
- Less flexible in protocol customization, mainly focused on user auth.
PocketBase SDK Authentication
- PocketBase is an open-source backend framework with built-in lightweight authentication supporting password, OTP, OAuth2 providers, and multi-factor authentication.
- Uses stateless JWT tokens sent with requests; no traditional server sessions.
- Authentication state is managed client-side with token storage and refresh.
- Supports superusers with impersonation and token generation for server-to-server use.
- SDKs provide direct API calls for auth flows and user management.
Pros:
- Simple, lightweight, and fully open-source backend.
- Multiple convenient auth methods easily configurable.
- Stateless token-based auth, easy for REST API usage.
- Supports multi-factor authentication and user impersonation.
Cons:
- Less fully featured and scalable than Logto or Firebase.
- No built-in UI; requires custom frontend auth flow.
- No dedicated token verification endpoint (uses token refresh for validation).
- More suitable for small-medium projects or embedded auth in local backends.
| Feature / Platform | Logto | Firebase Authentication | PocketBase SDK |
|---|---|---|---|
| Type | Open-source OIDC/OAuth provider | Managed Backend Auth-as-a-Service | Open-source backend with SDK |
| Authentication Methods | OAuth 2.1, OIDC, Social, SAML | Email/Password, Phone, Social providers | Password, OTP, OAuth2, MFA |
| Session Management | Token-based with API routes | Token & Session managed by SDK/backend | Stateless JWT; client manages tokens |
| Complexity | High (advanced protocols/features) | Low (ease of integration, Firebase ecosystem) | Medium (custom code needed) |
| Scalability | High (enterprise-ready) | Very High (Google Cloud scale) | Moderate (small to mid-size apps) |
| Extensibility | High (Management API, custom IdP) | Moderate (Firebase Extensions) | Moderate (custom backends) |
| Pricing | Free self-hosted or cloud plans | Usage-based pricing, can be costly at scale | Free self-hosted |
| Best for | SaaS, Enterprise, AI apps | Apps needing rapid setup & Firebase ecosystem | Lightweight apps, embedded servers |
This setup can be call, considering that MermaidJS allow to write themes https://sli.dev/guide/write-theme
So plugging the AI + custom theme, can be amazing for an Enterprise version!
| Platform | Type | Best for… | Key Differentiator |
|---|---|---|---|
| Clerk | AaaS | Modern web apps, startups, and developers who want a quick, easy, and aesthetically pleasing solution. | Best-in-class, pre-built UI components and a focus on developer experience. |
| Okta | IAM | Large enterprises and organizations with complex security and identity management requirements. | The most comprehensive, enterprise-grade identity platform on the market. |
| Auth0 | AaaS/IAM | Developers building applications that need flexible and customizable authentication. | Powerful extensibility with “Actions” and a wide array of social connections. |
| Logto | Open-source IAM | Teams that want a free, self-hostable, and transparent alternative to proprietary services. | Full control over your data and infrastructure with an active open-source community. |
FAQ
In Logto (and generally in web development), the difference between a traditional web app ~MPA and a single-page application (SPA) lies in how they load and render content:
Traditional web apps (also called multi-page apps or MPAs) render pages entirely on the server. Each user action like clicking a link or submitting a form causes the browser to request a new page from the server, which returns the full HTML for that page. This approach works well for simple apps with mainly read-only content and benefits from being SEO-friendly and able to function without JavaScript.
SPAs load a single HTML page initially and dynamically update the content within that page as users interact, without full page reloads. SPAs rely heavily on client-side JavaScript frameworks (like React or Vue) to fetch and render data on the fly, offering a smooth, app-like user experience that is highly interactive and fast.
SPAs require JavaScript support and are more complex to develop and optimize, particularly for SEO.
Why it matters in Logto and general application scenarios:
Traditional web apps suit use cases with simple or read-only client-side interactions, public-facing sites where SEO and discoverability are priorities, or where users might have limited JavaScript support.
SPAs are better for rich, highly interactive user interfaces, applications requiring complex features like live data updates, and scenarios where responsive and smooth user experiences are critical.
Choosing the right model affects development effort, performance, user experience, SEO, and how the app interacts with authentication and authorization services like Logto.
In sum, Logto differentiates these to guide developers on how best to integrate authentication flows depending on whether their app is traditional server-rendered or SPA, ensuring security and user experience are optimized for the app type.[1][2
How to create an SliDev-Editor
My Initial requirements for the SliDevJSEditor for Cursor 📌
We want to build a local-first markdown editor for SliDev presentations
The application should be built with a focus on an efficient content edition via markdown, specifically for SliDEVJS.
Core Requirements - The following features are mandatory for the initial build of the application, which should be created in the root of the repo.
Folder Selection: The user must be able to select a local folder to scan for files inside ./slidev.
This should be implemented via a visible input field or a file picker dialog, by default, it can be ./slidev/slidev-sample
File Tree/List: After selecting a folder, the application must display the related slides.md. If a toggle is ON, a full a list of all .md and .mdx files found within that folder will also be visible to select.
Side-by-Side Editor: When a file is selected from the list, the ToastUI Editor should open on the right-hand side of the screen, with the file list remaining visible on the left.
Editor Functionality: The ToastUI Editor must be fully functional, including markdown editing, saving the .md or .mdx to local storage and a live preview of the content.
Focus Mode: A button or toggle that hides the file list, expanding the editor to full width for a distraction-free writing experience.
File Saving: The application must have a clear mechanism to save the current editor content directly back to the selected local .md or .mdx file.
We can use NextJS as backend as it should be easier to integrate with Slidev than fastAPI.
Consider that the main page of the app will be a landing page, where we describe what it does.
Then it will have a path called /app, where all the editor will be visible and in /app/slidev/slidev-example we will see the statically render of the presentation
Make the UI layout look sleek and modern (gradients and all goodies).
Make it also mobile friendly.
You can also add the docker containers setup with a Dockerfile.dev a docker-compose.dev.yml and a Makefile with just 3 commands: spin the nextjs editor baremetal, another to build the container and another to build and run the container within this dev mode.
Good-to-Have Features - I did not mentioned these on the first go
These features are highly recommended to elevate the user experience and create a more complete tool.
Frontmatter Editor: A dedicated UI panel, separate from the main markdown content, for editing a file’s frontmatter (e.g., title, date, tags, description). This prevents syntax errors and provides a structured way to manage metadata.
Asset Handling: The ability to drag and drop images directly into the editor. The application should handle placing the image file into a specified local directory (e.e., src/assets/images) and automatically insert the correct markdown link into the document.
File Management: Add basic file management capabilities such as creating new files, creating new folders, and deleting existing files directly from the UI.
I got this after the first iteration:
git init
git branch -m main
git config user.name
git config --global user.name "JAlcocerT"
git config --global user.name
git add .
git commit -m "Initial commit: Starting slidev-editor via NextJS and ToastUI"
#sudo apt install gh
gh auth login
gh repo create slidev-editor --private --source=. --remote=origin --push
#git init && git add . && git commit -m "Initial commit: Starting astro editor via NextJS and ToastUI" && gh repo create astro-editor --private --source=. --remote=origin --pushOn this one, created main for the base functionalities of a markdown editor for slidev and created branches to test few authentication methods.
node --versionnpm init slidev #yarn create slidev
npm run dev
#npm run dev -- --host 0.0.0.0 --port 4321 #http://192.168.1.11:4321/
#rm -rf .git
npm run build
#cd ./dist
#npx serveKPIs for SaaS
- LTV
- CAC
People say to aim for LTV > 3*CAC